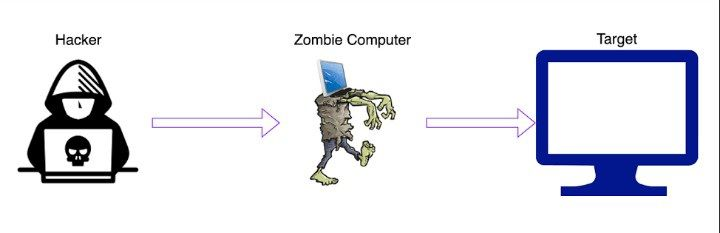
Introduction to Jombie IP
In the ever-evolving landscape of cybersecurity, the emergence of Zombie IP has become a significant concern for both individuals and organizations alike. This term refers to a malicious tactic employed by cybercriminals to leverage compromised internet protocol (IP) addresses that have been hijacked or spoofed. The name “Jombie” derives from the idea of a digital “zombie,” where infected devices are manipulated to carry out harmful activities without the knowledge of their owners.
The prevalence of Jombie IP attacks is alarming; they have surged in frequency as hackers exploit vulnerabilities in digital systems. Often, these attacks are orchestrated by black hat hackers who manipulate networks to execute fraudulent activities such as data breaches, identity theft, and denial-of-service attacks. As digital platforms continue to integrate into essential operations across various sectors, the threats posed by such malicious activities elevate the demand for robust cybersecurity measures.
Moreover, the increasing sophistication of these cyber threats underscores the importance of ethical hacking practices designed to counteract Jombie IP challenges. Organizations, including those involved in Cisco CCNA training and certification programs, are actively developing strategies to fortify their networks against these types of attacks. These initiatives not only involve the deployment of advanced cybersecurity tools but also emphasize the need for a proactive defense approach.
This blog post aims to explore the mechanics of Jombie IP, its expanding presence in the cyber world, and the steps that can be taken to mitigate its impacts. By understanding the critical aspects of this innovative threat, readers can better appreciate the imperative for comprehensive cyber strategies that prioritizes safety and security in an interconnected realm.
How Jombie IP Works
The phenomenon known as Jombie IP is a malicious entity within the realm of cybersecurity, primarily associated with the application of black hat techniques. This occurs when attackers exploit the intricacies of internet protocol (IP) addresses to facilitate various forms of cyber attacks, including hacking attempts that infiltrate networks, exploit vulnerabilities, and compromise sensitive data. Understanding how Jombie IP operates involves examining the mechanisms that underpin its existence and functionality.
At its core, Jombie IP is created when cybercriminals acquire, manipulate, or hijack legitimate IP addresses. This manipulation often occurs through methods such as IP spoofing, which allows attackers to masquerade as trusted devices. By sending requests from a forged IP address, they can bypass security measures, subsequently leading to unauthorized access. Attackers utilize this technique to infiltrate network systems, install malicious software, and retrieve sensitive information without detection.
The methods employed by these malicious actors often extend beyond simple address manipulation. Attackers may leverage automated scripts or botnets to generate large volumes of Jombie IP requests, overwhelming target systems. This flood of traffic not only disrupts normal operations but can also serve to mask more insidious activities, such as data exfiltration. The types of data compromised through these attacks can range from personal identifiable information (PII) to confidential corporate data, posing significant risks to individual privacy and organizational integrity.
Therefore, the implications of Jombie IP are profound. For individuals, the risk of identity theft increases dramatically, while organizations face potential financial losses, reputational damage, and legal ramifications. Comprehensive understanding alongside effective countermeasures is vital for enhancing cybersecurity and mitigating the threats posed by Jombie IP in an increasingly digital landscape.
Impact on Personal Privacy
The emergence of Jombie IP poses significant risks to personal privacy. Cybercriminals exploit these malicious techniques to divert a user’s Internet Protocol (IP) address, allowing them to masquerade as legitimate users. This manipulation of IP addresses is a common tactic employed by black hat hackers seeking to gain unauthorized access to sensitive information. The implications are severe, as individuals’ personal data, including financial records and sensitive communications, can be compromised. Individuals risk falling victim to identity theft, where their personal information is exploited for fraudulent purposes, further leading to potential financial loss and damage to credit scores.
Risks to Cybersecurity
In addition to personal privacy concerns, Jombie IP significantly jeopardizes overall cybersecurity. Organizations relying on Cisco systems and CCNA protocols are increasingly targeted by attackers using such techniques. Unauthorized access can disrupt online services, leading to operational downtime and loss of critical data. Organizations may also face reputational damage as customer trust erodes following a security breach. Furthermore, the manipulation of IP addresses can serve as a gateway for additional cyberattacks, including distributed denial-of-service (DDoS) attacks that overwhelm network infrastructures. This complexity underscores the importance of robust cybersecurity measures, including ethical hacking practices to identify and remediate vulnerabilities before they can be exploited.
Motivations Behind Jombie IP Attacks
The motivations fueling Jombie IP attacks are varied, reflecting a landscape of both financial gain and espionage. Cybercriminals may use these tactics to commit fraud or steal sensitive, proprietary information, benefiting their malicious intent. In an age where data is a valuable commodity, such motives demonstrate a concerning trend in the cyber landscape. Moreover, state-sponsored actors may employ Jombie IP techniques for espionage purposes, targeting organizations with access to confidential information. Understanding these motivations is crucial for individuals and organizations alike in the ongoing battle against such cyber threats.
Signs of a Jombie IP Infection
Identifying a Jombie IP infection is crucial for maintaining cybersecurity. There are several indicators that may suggest your system has been compromised, allowing cybercriminals to exploit vulnerabilities through the manipulation of IP addresses. One primary sign is unusual network activity, which can manifest as unexpected traffic spikes or unusual external access attempts to devices within your network. If you notice an increase in data transfer that does not align with your usage patterns, this may indicate that unauthorized entities are using your IP address.
Another significant red flag is compromised user accounts. If you receive notifications about login attempts from unfamiliar locations or see changes made to account settings without your knowledge, this may point to a breach. Cybersecurity practices emphasize the importance of maintaining strong passwords and multi-factor authentication to mitigate the risk of these accounts being hijacked, particularly in scenarios involving Jombie IPs.
Moreover, an increase in system crashes or performance degradation can be a sign of a Jombie IP infection. Malware often accompanies such infections, leading to black hat hacking practices that can degrade the performance of your systems. Slow response times, unresponsive applications, or frequent disconnections can suggest that your network is under attack.
Lastly, unexpected changes in device configurations may also signal an infection. If firewall settings or security policies are altered without your intervention, it is advisable to conduct a thorough review of your network’s security measures. Engaging in ethical hacking practices, such as routine scans and penetration tests, can uncover vulnerabilities that might allow a Jombie IP to infiltrate your network.
Being vigilant and aware of these signs is essential in combating Jombie IP infections and enhancing overall cybersecurity efforts.
How to Get Rid of Jombie IP
To effectively eliminate Jombie IP from infected systems, users must follow structured and methodical steps targeting both the immediate threat and long-term prevention. Start by conducting a comprehensive diagnostic of your system to identify all potential vulnerabilities that cyber attackers could exploit. Employ trusted cybersecurity software capable of detecting and removing malware, specifically designed with features that protect against both black hat tactics and ethical hacking attempts.
Once you have selected the appropriate software, run a full scan of your system. Tools like Cisco’s security solutions provide robust features for identifying Jombie IP and similar threats. Most of these tools will classify threat types and help isolate any malicious entities. After the initial scan, proceed to remove identified threats, following any prompts provided by the software. Ensure that quarantined items are thoroughly assessed before final deletion to prevent unintended data loss.
Next, consider implementing a firewall and an intrusion detection system to monitor incoming and outgoing traffic continuously. These systems act as formidable barriers against unauthorized access and can preemptively stop potential Jombie IP attacks from infiltrating your network. Regular updates of your operating system and security software are essential to patch any vulnerabilities that hackers could exploit, enhancing overall cyber security.
To ensure your system remains impervious to future infections, foster safe online behavior. Avoid engaging with suspicious links or downloads, and educate all users about the signs of phishing and other cyber threats. Backing up critical data regularly can also serve as an excellent recovery strategy. By taking these steps, you will not only rid your system of Jombie IP but also fortify your defenses against similar threats in the future.
Prevention Strategies Against Jombie IP
As cyber threats continue to evolve, it is crucial for individuals and organizations to implement proactive measures to protect themselves from becoming victims of Jombie IP. The incorporation of robust security protocols can significantly mitigate the risk associated with this form of attack.
One of the fundamental strategies in preventing Jombie IP attacks is the use of strong, unique passwords. Passwords should be a combination of letters, numbers, and special characters and should not be easily guessable. Password managers can also assist in generating and storing complex passwords securely. Regularly updating these passwords further fortifies security against potential breaches.
In conjunction with password management, regular software updates are essential. Cybercriminals often exploit vulnerabilities in outdated software, which can serve as gateways to attacks like Jombie IP. Ensuring that operating systems, applications, and antivirus software are consistently updated with the latest security patches can minimize these risks significantly.
Utilizing firewalls is another effective preventative measure. Firewalls act as a barrier between a trusted network and untrusted external networks, filtering incoming traffic to prevent unauthorized access. Organizations may also consider adopting advanced firewalls that offer additional protections against sophisticated cyber threats.
Employing Virtual Private Network (VPN) services enhances cyber security by encrypting internet traffic, thereby safeguarding sensitive information from prying eyes. A VPN creates a secure connection, making it more challenging for malicious entities to identify and exploit vulnerabilities linked to IP addresses.
Finally, staying informed about the latest cyber threats is essential. Regularly consulting trusted cybersecurity resources can provide invaluable information on emerging threats, thus enabling individuals and organizations to adjust their security measures accordingly. Being proactive about cyber security education and awareness will help in significantly reducing the likelihood of falling victim to Jombie IP or similar attacks.
Legal and Ethical Considerations of Jombie IP
The emergence of Jombie IP attacks has raised significant legal and ethical concerns within the realm of cybersecurity. Legally speaking, individuals engaging in Jombie IP activities may be subject to criminal prosecution under various statutes related to cybercrime. In many jurisdictions, these attacks involve unauthorized access to computer systems, data theft, and other illicit actions that can lead to severe penalties, including imprisonment and hefty fines. With laws such as the Computer Fraud and Abuse Act (CFAA) in the United States, perpetrators of Jombie IP attacks may face substantial legal repercussions. The enforcement of these laws aims not only to punish offenders but also to deter future cybercriminals, thereby promoting a safer digital environment.
On the other hand, the victims of Jombie IP attacks are entitled to legal protections. Depending on the specific circumstances surrounding an attack, victims may pursue civil remedies, including compensation for damages incurred due to unauthorized access or data breaches. This legal framework is vital in ensuring that organizations and individuals have recourse to recover losses and hold attackers accountable, thus reinforcing the importance of accountability in the strict domain of cybersecurity.
Ethical considerations also play a crucial role in the discussion surrounding Jombie IP. Ethical hacking practices, endorsed by organizations like Cisco and individuals holding relevant certifications, reinforce the imperative to operate within the bounds of the law while combating cyber threats. Cybersecurity professionals, often categorized as ethical hackers or “white hats,” are tasked not only with defending systems from threats but also with promoting ethical standards within the industry. Conversely, the actions of “black hat” hackers, who engage in Jombie IP attacks, present a contrasting perspective that often undermines trust in digital ecosystems. Ultimately, fostering a culture of ethical responsibility among cybersecurity professionals is paramount in the ongoing battle against threats like Jombie IP.
The Role of Haxygen Team in Combating Jombie IP
The Haxygen team has emerged as a prominent entity in the fight against Jombie IP threats, leveraging their deep expertise in cybersecurity and ethical hacking. Composed of skilled professionals proficient in an array of fields such as network security, software development, and malicious behavior analysis, the team is dedicated to developing and implementing effective countermeasures to safeguard both individuals and organizations from the silent and pervasive nature of Jombie IP attacks. These individuals hold prestigious certifications like Cisco’s CCNA and other recognized cyber-security credentials, which equip them with the knowledge required to identify and mitigate such risks.
One of the prime objectives of the Haxygen team is ongoing research into the methodologies used by black hat hackers to exploit vulnerabilities in various systems. By studying these malicious tactics, they can craft sophisticated defenses against Jombie IP attempts. The team continuously updates its knowledge base with emerging threats and develops tools that empower users to secure their networks. These tools range from advanced firewalls to innovative intrusion detection systems, all designed to deter unauthorized access and enhance overall cyber security.
In addition to their technological developments, the Haxygen team actively engages in community outreach and education initiatives. They provide training sessions and workshops aimed at increasing cyber awareness among businesses and the general public. Through these efforts, the Haxygen team not only informs users about the dangers associated with Jombie IP but also promotes best practices for maintaining a secure online environment. By fostering such awareness, they aim to diminish the impact of cyber threats, thereby fortifying defenses against potential breaches and ensuring a more secure cyberspace for all.
Conclusion: Staying Aware and Vigilant
Throughout this discussion on Jombie IP, we have explored the intricacies of this cyber threat, its implications for security, and the proactive measures one can take to defend against it. Jombie IP refers to a malicious technique used by cybercriminals, often associated with black hat hacking activities, to manipulate IP addresses for illicit purposes. Understanding the mechanics of such threats is crucial in today’s digital landscape where ethical hacking and cybersecurity are increasingly paramount.
Cybersecurity is not a static field; it demands continuous learning and adaptation. As we have noted, many individuals and organizations have fallen victim to Jombie IP due to a lack of awareness and preparedness. By familiarizing oneself with the characteristics of Jombie IP attacks and their potential impact, users and organizations can mitigate risks more effectively. Awareness can lead to enhanced vigilance, which is essential in recognizing indicators of such threats early on.
To combat Jombie IP successfully, it is imperative to implement robust security measures and stay informed about the latest trends in cyber risks. Engaging with skilled professionals who specialize in cybersecurity, such as those found in teams like Haxygen, can provide the necessary insights and strategies to manage these threats adeptly. Understanding the distinctions between ethical hacking, black hat tactics, and the role of certifications like Cisco CCNA can further empower individuals to navigate the complex cyber terrain.
In light of the ever-evolving threat landscape, we encourage readers to remain proactive in bolstering their security. Investing in knowledge and assistance from cybersecurity experts will not only guard against Jombie IP attacks but also foster a culture of security awareness that can benefits both individuals and organizations in the long run.





